Table of Contents
Everyday IT decisions create hidden security risks by leaving small gaps unnoticed. This article explains how those gaps form and outlines practical steps organizations can take to strengthen defenses effectively.
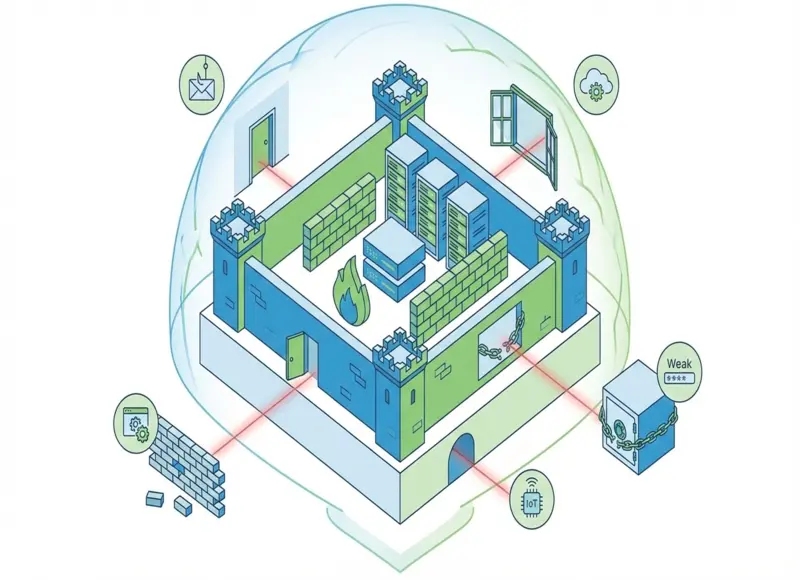
IT teams often focus on major threats and miss small gaps that weaken daily defenses. These gaps hide in routine work, fast growth, and shared systems. Over time, they create risk without clear warning signs.
Organizations protect their systems better when they spot and close the security gaps they often overlook. This article explains how common blind spots form across cloud use, devices, software, vendors, and policies, and why basic controls are not enough. It sets the stage for practical steps that strengthen security beyond surface-level fixes.
1) Misconfigured cloud storage permissions
Teams often set cloud storage permissions too wide. They do this to speed up work or fix access issues. These settings can leave data open to the public or to too many internal users.
Public read or write access remains a common problem. Storage buckets may expose files by mistake, including backups and logs. Attackers search for these openings and download data fast.
Identity and access settings also cause risk. Roles may grant more rights than needed, or old accounts may stay active. These gaps let unauthorized users move data or change settings.
Shared responsibility adds to the issue. Cloud providers secure the platform, but customers control access. When teams assume the provider handles permissions, mistakes go unnoticed.
Simple checks reduce risk. Teams can limit access by role, review permissions often, and block public access by default. Alerts for permission changes also help catch errors early.
2) Untracked shadow IT devices
Untracked shadow IT devices include personal laptops, phones, tablets, and smart devices used for work without IT approval. Teams often use them to move faster or avoid delays.
These devices sit outside standard security controls. IT teams cannot confirm updates, encryption, or endpoint protection. That gap increases the chance of data exposure.
Employees may connect these devices to company networks or cloud apps. Sensitive data can move to systems that lack proper access rules. Logging and monitoring often fail to capture this activity.
Shadow IT devices also create compliance risks. Regulations often require control over where data lives and who can access it. Unapproved devices make it harder to meet those rules.
Asset inventories rarely include these devices. When a device is lost or an employee leaves, IT may not know what data remains on it. That limits the ability to respond quickly to incidents.
Clear device policies and simple approval paths reduce this risk. Visibility tools also help teams find and manage unknown devices before they cause harm.
3) Outdated software and unpatched systems
Outdated software creates quite security gaps across IT environments. Vendors stop releasing fixes after support ends, which leaves known flaws open to attack. Teams often miss these risks because systems still appear to work.
Unpatched systems give attackers an easy entry point. They target known bugs with ready-made tools, including malware and ransomware. Even one missed update can expose shared networks and data.
Older platforms also weaken endpoint security. Devices may no longer receive threat definitions or system updates. This gap reduces the ability to block new attacks.
Outdated software can raise compliance and audit risks. Many standards require timely patching and supported systems. Falling behind can increase costs during reviews and incident response.
Shadow IT makes the problem worse. Teams may run legacy apps that security tools do not track well. These blind spots delay detection and slow response when incidents occur.
4) Weak third-party vendor controls
Many organizations rely on vendors for IT services, support, and tools. These vendors often need access to systems or data, which can expand the attack surface.
Teams may trust vendors without checking their security practices. This gap grows when contracts lack clear security rules or when reviews happen only once.
Poor access control creates another risk. Vendors may keep broad or permanent access even after a project ends, which raises the chance of misuse or mistakes.
Limited monitoring also weakens security. If teams do not log vendor activity, they may miss early signs of a problem.
Strong vendor controls require regular checks. Companies can review security posture, limit access to only what vendors need, and remove access on time.
Clear ownership matters as well. Even when a breach starts with a vendor, the organization still carries the risk and the impact.
5) Inconsistent security policy enforcement
Inconsistent policy enforcement weakens security even when strict rules exist. Teams apply controls differently across departments, locations, and systems. These gaps create uneven protection.
Hybrid environments add risk. On?premises systems may follow strict rules, while cloud tools use looser settings. Shadow IT often bypasses approval and skips required controls.
Policy exceptions also grow over time. Staff approve quick fixes and forget to review them. These exceptions turn into permanent holes.
Lack of visibility makes the problem worse. Without centralized monitoring, teams cannot see where policies fail. Security teams then react to incidents instead of preventing them.
Regular audits help expose gaps. Clear ownership and simple standards improve consistency. When teams enforce the same rules everywhere, security becomes more reliable.
Understanding Overlooked Gaps in IT Security
Many IT security failures start with small misses that teams ignore or do not see. These gaps grow when tools, people, and processes fall out of sync across systems and vendors.
Common Causes of Security Oversights
Teams often add tools faster than they review settings. This creates unused rules, weak access controls, and alerts that no one checks.
Other common causes include:
- Policy drift from one-off exceptions that stay in place
- Shadow IT occurs when staff use apps outside approved systems
- Unsecured remote access was left open after role changes
- Third?party access without regular reviews
Limited testing also plays a role. Routine scans miss real-world attack paths. Red teaming exposes IT vulnerabilities by simulating how attackers chain small flaws into a breach. Red team tools help teams find gaps that standard checks miss.
Potential Impact on Organizational Risk
Overlooked gaps raise the chance of data loss, service outages, and fraud. Attackers often exploit simple weaknesses, not advanced flaws.
These gaps can lead to:
- Account takeovers from weak identity controls
- Data leaks through vendors with poor security
- Ransomware spread due to flat networks
Risk grows when teams underestimate impact. A single gap can affect many systems at once. Downtime slows operations. Breaches trigger legal duties and fines. Trust drops with customers and partners. Addressing gaps early reduces both technical and business damage.
Strengthening IT Security Beyond the Basics
Strong security needs steady checks and people-focused controls. Teams reduce risk when they watch systems in real time and guide staff to make safer choices.
Continuous Monitoring and Assessment
Many teams set controls once and move on. That leaves gaps as systems change. Continuous monitoring spots weak points early and limits damage.
They should track logs, alerts, and access across networks, cloud tools, and endpoints. Simple dashboards help teams see unusual sign-ins, data moves, and failed updates.
Key actions that matter:
- Run regular security scans and short risk reviews
- Patch systems on a set schedule
- Review access rights after role changes
- Test backups and recovery steps
Assessments should happen after major changes, not once a year. Frequent checks keep controls aligned with how the business actually runs.
Integrating Human Factors Into Security Strategy
People cause many security failures, often by mistake. Teams must design security with daily work in mind.
Clear rules help staff act fast and correctly. Short training sessions work better than long lectures. They should focus on real risks like phishing, weak passwords, and unsafe file sharing.
Effective people-focused controls include:
- Phishing drills with quick feedback
- Simple password rules with managers
- Limited access based on job needs
- Easy ways to report suspicious activity
Leaders should support safe behavior, not punish errors. When staff feel responsible and informed, security improves across the organization.
Recent Blogs
The Role of Artificial Intelligence in Modern Law Firm Growth Strategies
-
03 Mar 2026
-
6 Min
-
104
How Custom Software Companies Help Enterprises Automate Complex Workflows
-
03 Mar 2026
-
5 Min
-
127